Design of a Distributed Intrusion Reaction System Employing Intel vPro Technology
We have implemented a preliminary version of the design proposed in [1] in order to demonstrate how the solution performs in a real scenario. The developed prototype implements some of the main features described throughout said paper. Basically, we have built an operative environment that contains computers employing Intel vPro (versions 2.6, 3.0 and a beta testing 6.0 version of Intel AMT) connected to a local switched network. The IRS Agent subsystem have been partially implemented using the Intel AMT SDK and Mobile C. The Intel AMT SDK provides access to the functionality offered by Intel AMT, while Mobile C has been used for creating reactive actions that can be propagated to other computers in the network.
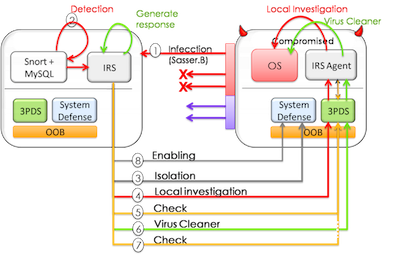
To test the effectiveness of the solution under a realistic attack scenario, we have infected a machine with the Sasser virus which will try to infect computers in the neighborhood. The detection mechanism will generate an alert regarding this propagation traffic and the IRS software will react to this incident by isolating the compromised system, executing commands for retrieving evidences and disinfecting the system, and enabling the host system in the network.
The steps shown in the video are the following:
References
- Ana Nieto and Gerardo Fernandez (2012): Sistema Colaborativo de Detección y Reacción ante Intrusiones basado en Intel vPro. In: XII Reunión Española sobre Criptología y Seguridad de la Información (RECSI 2012), pp. 45-50, San Sebastián, 2012, ISBN: 978-84-615-9933-2.

