Industrial Security
The industrial security line embraces all those activities that address best practices and protection measures for the precise performance of industrial environments and its supply chain, the functions of which normally operate in complex infrastructures, relevant for social and economic well-being. This also means that any security risk and/or threat may imply the interruption partial or total of relevant actions, with serious repercussions for business continuity. Probably one of the factors that may lead to these risks is precisely the digital transformation that encompasses today’s most innovative and new industrial paradigms, such as Industry 4.0/5.0.
Industry 4.0/5.0 constitutes a ground-breaking change in current operational processes and industrial environments, as also depicted in Fig. 1, but also a change to consider new research challenges. One of these challenges is the need to create environments capable of regulating operational actions under the premise of “coexistence” with the legacy elements, and under the conditions of sustainability, human centrality and resilience. The way to connect the physical and real worlds is provided by the new concept of Cyber-Physical Systems (CPS), whose looped functions can be monitored and controlled by disruptive technologies and infrastructures, such as digital twins, blockchain, AI, cloud/edge and 6G. The idea is to streamline the processing and storage of critical data in a synchronized and controlled manner, but also to ensure remote access. However, when such connectivity paves the way for asynchronous communication, supported by IoT paradigms, such as the Industrial Internet of Things (IIoT), the coexistence and convergence of technologies (IT-OT) becomes increasingly necessary [1], giving rise to “smart” ecosystems, attractive to attackers [2].
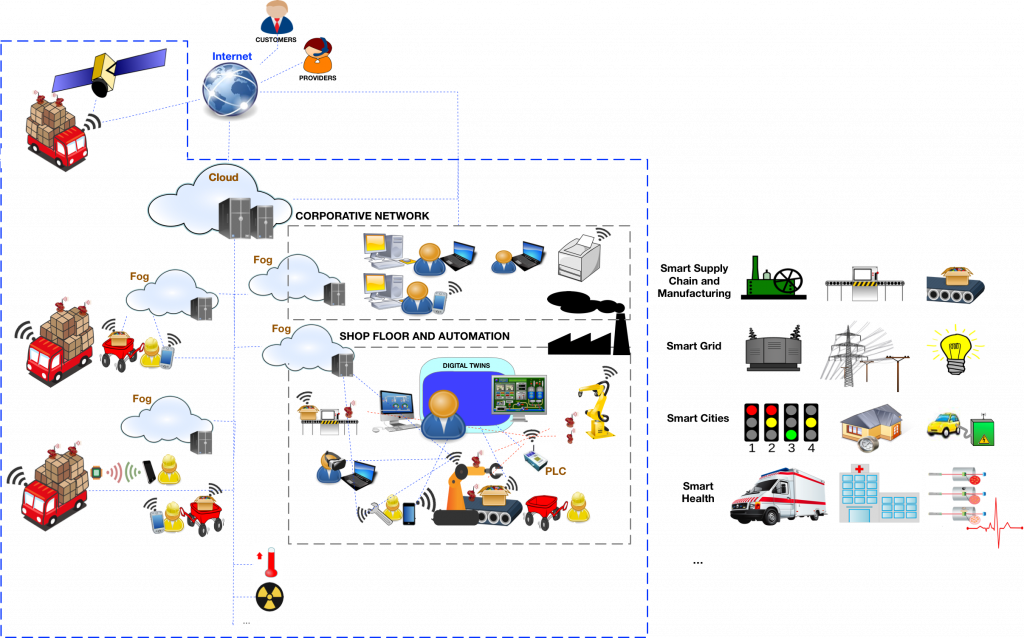
In this sense, NICS Lab has shown experience in the field of CPS/IIoT protection, starting its research in the field of Industrial Control Systems (ICS) in 2007 [3], and continuing today with industrial security, thanks in part to its extensive participation in multiple national and international R&D projects. Most of these projects focus mainly on the secure control of systems with applications in energy and manufacturing, which have allowed us to investigate issues related to secure interconnection of systems, access control, situational awareness and resilience, all supported by the aforementioned technologies.
In the last decade, NICS Lab has been heavily involved in several R&D projects within the energy sector, developing expertise in the interconnection of critical systems under diverse access control approaches. This is the case of PERSIST and PISCIS, where the team proposes an access control technique based on RBAC under roles defined in the IEC-62351-8 standard and the context [4], thereby favoring the deployment of a trustworthy platform supported by a set of services linked to prediction, trust and privacy. Moreover, with PERSIST the team raised the need to study stealth attacks and their classification [5], to subsequently consider them in the analysis of the de-facto OCPPv1.6 protocol for electric vehicle infrastructures [6]. The work in PERSIST also allowed us the prior selection of privacy-preserving schemes [7] providing later its automatic recommender [8], as well as the optimal restoration of control after possible attacks [9] with impact also on access control [10].
The experience gained facilitated NICS Lab’s intense participation in the European project SeleadGrid, in order to explore how to interconnect constrained elements in complex and dynamic scenarios [11]. Thus, exhaustive analyses on possible threats to energy control were raised [12], but also several protection proposals to be integrated as part of the interconnection process. For example, secure peer-to-peer communication taking into account the restrictive nature of Smart Grid devices and the likelihood of stealthy attacks for exfiltration [13], and access control guided by contextual states at the time of access and according to past actions validated by a blockchain network. The latter work required, in addition, a previous analysis on the relevance of the blockchain network for Smart Grid-based environments and its control [14].
Similarly, the Smart and Secure EV-Urban Lab project (Smart Secure I, Smart Secure II in which NICS Lab acted as main coordinator) focused on the dynamic management and monitoring of microgrids and electric vehicle charging infrastructures (mainly supported by OCPPv2.0.1), facilitating the provision of a real laboratory for the community. The laboratory is not only able to produce energy according to the most recommended sustainability standards, but also adds agent-based security mechanisms to control energy theft and fraud [15]. The nature of these threats necessarily led to an exhaustive study on their impact attending to the STRIDE+DEAD methodology for OCPPv2.0.1 [16], but also to the actual usefulness of some disruptive technologies (AI, Big Data, Blockchain and software agents) for prevention [17].
Last but not least, it is relevant to highlight the involvement of NICS Lab in DUCA and CyberSecPro. Through DUCA, the team has extended its industrial security portfolio by providing to the consortium an Audit Manager capable of providing auditing actions under a controlled blockchain network to be tested in Smart Grid and Transport scenarios. However, without an adequate awareness and culture of cybersecurity applied to the multiple applications of the energy sector, it is difficult to arrive at appropriate strategic solutions. CyberSecPro therefore raises the imminent need to train industry professionals in cybersecurity to align disciplines and ensure resilience, security and privacy.
In the field of manufacturing, NICS Lab shows efforts in several topics. For example, interconnection of Industry 5.0 digital twins (SecTwin 5.0), access control (SADCIP) [18], and ethical hacking and penetration testing (eMapa 4.0-I and eMapa 4.0-II). In the latter project, NICS Lab was responsible for the justification of the approach with respect to the state of the art, the extraction of requirements and the validation of the resulting pentesting platform. Similar actions were carried out in NERV, but focusing research on cyber-intelligence and OSSINT with application in the new business contexts of Industry 4.0. In the supply chain of these manufacturing systems, NICS Lab has also been involved in its corresponding roadmap established as part of CyberSec4Europe [19], the creation and maintenance of blockchain networks and nodes for this sector, and the extraction of security requirements according to a preestablished and rigorous methodology [20]. Also, and thanks to DIIS-IoT, the team has accelerated its involvement in the deployment of IIoT devices by launching the IIoT-Tesbed within its domain. With DIIS-IoT, some initiatives were carried out, such as the identification of security and privacy issues in IIoT-based ecosystems [21], and the exploration of interoperability issues caused by IIoT [2] and CPS [22]-based systems.
Although these are the team’s most widespread fields, NICS Lab has also developed expertise in the area of dominance with CAIN, where research has focused on restoring the structural controllability after attacks [23], and in the field of health industry with CYBSEC-TECH where the team has explored the security needs of the medical IIoT/CPS devices, validating the resulting cybersecurity platform. But also, we have conducted other initiatives beyond the umbrella of R&D projects, such as the co-supervision of a PhD thesis together with the University of Piraeus in order to address the comprehensive protection of critical IoT/IIoT-dependent systems. Among the most remarkable results, it is worth mentioning the extended IoT/IIoT study for the protection of critical infrastructures and their possible threats [24], but also the subsequent risk management analyses considering the CPS constraints [25].
References
- Javier Lopez and Cristina Alcaraz and Jesús Rodriguez and Rodrigo Roman and Juan E. Rubio (2017): Protecting Industry 4.0 against Advanced Persistent Threats. 2017.
- Cristina Alcaraz (2019): Secure Interconnection of IT-OT Networks in Industry 4.0. In: Critical Infrastructure Security and Resilience: Theories, Methods, Tools and Technologies, pp. 201-217, Springer International Publishing, 2019, ISBN: 978-3-030-00024-0.
- Cristina Alcaraz and Sherali Zeadally (2013): Critical Control System Protection in the 21st Century: Threats and Solutions. In: IEEE Computer, vol. 46, no. 10, pp. 74 – 83, 2013, ISSN: 0018-9162.
- Cristina Alcaraz and Javier Lopez and Stephen Wolthusen (2016): Policy Enforcement System for Secure Interoperable Control in Distributed Smart Grid Systems. In: Journal of Network and Computer Applications, vol. 59, pp. 301–314, 2016, ISSN: 1084-8045.
- Lorena Cazorla and Cristina Alcaraz and Javier Lopez (2018): Cyber Stealth Attacks in Critical Information Infrastructures. In: IEEE Systems Journal, vol. 12, pp. 1778-1792, 2018, ISSN: 1932-8184.
- Cristina Alcaraz and Javier Lopez and Stephen Wolthusen (2017): OCPP Protocol: Security Threats and Challenges. In: IEEE Transactions on Smart Grid, vol. 8, pp. 2452 – 2459, 2017, ISSN: 1949-3053.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2017): Selecting Privacy Solutions to Prioritise Control in Smart Metering Systems. In: The 11th International Conference on Critical Information Infrastructures Security, pp. 176-188, 2017.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2017): Recommender System for Privacy-Preserving Solutions in Smart Metering. In: Pervasive and Mobile Computing, vol. 41, pp. 205-218, 2017, ISSN: 1574-1192.
- Cristina Alcaraz (2018): Cloud-Assisted Dynamic Resilience for Cyber-Physical Control Systems. In: IEEE Wireless Communications, vol. 25, no. 1, pp. 76-82, 2018, ISSN: 1536-1284.
- Cristina Alcaraz and Javier Lopez and Kim-Kwang Raymond Choo (2016): Dynamic Restoration in Interconnected RBAC-based Cyber-Physical Control Systems. In: Proceedings of the 13th International Joint Conference on e-Business and Telecommunications (SECRYPT 2016), pp. 19-27, Lisboa, 2016, ISBN: 978-989-758-196-0.
- Aristeidis Farao and Juan E. Rubio and Cristina Alcaraz and Christoforos Ntantogian and Christos Xenakis and Javier Lopez (2019): SealedGRID: A Secure Interconnection of Technologies for Smart Grid Applications. In: 14th International Conference on Critical Information Infrastructures Security (CRITIS 2019), pp. 169-175, Springer, Cham Springer, Cham, 2019, ISBN: 978-3-030-37669-7.
- Juan E. Rubio and Cristina Alcaraz and Javier Lopez (2018): Addressing Security in OCPP: Protection Against Man-in-the-Middle Attacks. In: 9th IFIP International Conference on New Technologies, Mobility & Security, 2018.
- Cristina Alcaraz and Giuseppe Bernieri and Federica Pascucci and Javier Lopez and Roberto Setola (2019): Covert Channels-based Stealth Attacks in Industry 4.0. In: IEEE Systems Journal., vol. 13, pp. 3980-3988, 2019, ISSN: 1932-8184.
- Cristina Alcaraz and Juan E. Rubio and Javier Lopez (2020): Blockchain-Assisted Access for Federated Smart Grid Domains: Coupling and Features. In: Journal of Parallel and Distributed Computing, vol. 144, pp. 124-135, 2020, ISSN: 0743-7315.
- Cristina Alcaraz and Alberto Garcia and Javier Lopez (2022): Implicaciones de seguridad en MAS Desplegados en Infraestructuras de Carga basadas en OCPP. In: VII Jornadas Nacionales en Investigación en Ciberseguridad (JNIC 2022), pp. 172-179, 2022, ISBN: 978-84-88734-13-6.
- Cristina Alcaraz and Jesus Cumplido and Alicia Triviño (2023): OCPP in the spotlight: threats and countermeasures for electric vehicle charging infrastructures 4.0. In: International Journal of Information Security, 2023, ISSN: 1615-5262.
- Cristina Alcaraz and Jesus Cumplido and Alicia Triviño (2021): Monitorización Segura en Infraestructuras de Carga de Vehículos Eléctricos Frente a Ciber-Ataques. In: Actas del XII International Greencities Congress, Greencities, Inteligencia y Sostenibilidad Urbana, & S-Moving, Movilidad Inteligente y Sostenible, pp. 17-30, FYCMA – Palacio de Ferias y Congresos de Málaga, 2021, ISBN: 978-84-09-19596-1.
- Javier Lopez and Juan E. Rubio (2018): Access control for cyber-physical systems interconnected to the cloud. In: Computer Networks, vol. 134, pp. 46 – 54, 2018, ISSN: 1389-1286.
- Rodrigo Roman and Cristina Alcaraz and Javier Lopez and Kouichi Sakurai (2023): Current Perspectives on Securing Critical Infrastructures’ Supply Chains. In: IEEE Security & Privacy, vol. 21, no. 4, pp. 29-38, 2023, ISSN: 1540-7993.
- Simone Fischer-Hübner and Cristina Alcaraz and Afonso Ferreira and Carmen Fernandez-Gago and Javier Lopez and Evangelos Markatos and Lejla Islami and Mahdi Akil (2021): Stakeholder Perspectives and Requirements on Cybersecurity in Europe. In: Journal of Information Security and Applications, vol. 61, no. 102916, 2021, ISSN: 2214-2126.
- Cristina Alcaraz (2019): Security and Privacy Trends in the Industrial Internet of Things. Springer, 2019, ISBN: 978-3-030-12330-7.
- Cristina Alcaraz and Javier Lopez (2017): Secure Interoperability in Cyber-Physical Systems. In: Security Solutions and Applied Cryptography in Smart Grid Communications, IGI Global, USA, pp. 137-158, IGI Global, USA, 2017, ISBN: 9781522518297.
- Cristina Alcaraz and Estefania Etcheves Miciolino and Stephen Wolthusen (2015): Multi-Round Attacks on Structural Controllability Properties for Non-Complete Random Graphs. In: The 16th Information Security Conference (ISC), pp. 140–151, Springer Springer, Springer International Publishing Switzerland, 2015.
- Ioannis Stellios and Panayiotis Kotzanikolaou and Mihalis Psarakis and Cristina Alcaraz and Javier Lopez (2018): Survey of IoT-enabled Cyberattacks: Assessing Attack Paths to Critical Infrastructures and Services. In: IEEE Communications Surveys and Tutorials, vol. 20, pp. 3453-3495, 2018, ISSN: 1553-877X.
- Ioannis Stellios and Panayiotis Kotzanikolaou and Mihalis Psarakis and Cristina Alcaraz (2021): Risk Assessment for IoT-Enabled Cyber-Physical Systems. In: Advances in Core Computer Science-Based Technologies, pp. 157-173, Springer International Publishing, Cham, 2021, ISBN: 978-3-030-41196-1.

